Univention Blog
News, Tipps and Best Practices
How to Integrate SAML Single Sign-On in ownCloud App
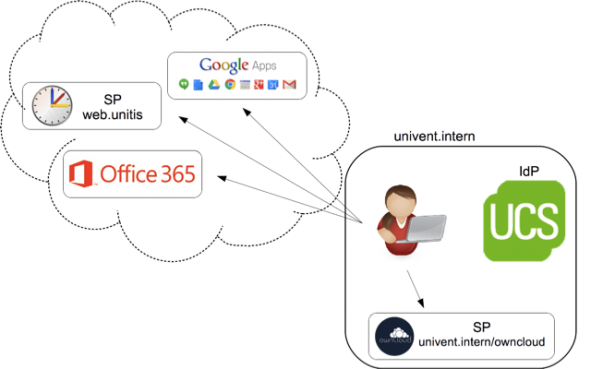
If you need to use various services online, which is by the way the norm, there’s nothing more conventient than using single sign-on (SSO). SSO allows you to log in to all available services in a domain with one password only. UCS provides this feature via the SAML Identity Provider since UCS 4.1. We chose to […]
EGroupware in the Univention App Center: Group Dynamics of Bits and Bytes
The Univention App Center makes it easy to install and set up a sophisticated collaboration solution on a stable basis. Univention Corporate Server (UCS) offers this basis – also for the integration with other open source solutions. EGroupware was created in 2003 and is thus one of the early collaboration solutions in the open source […]
Step by Step Guide to a Multi-Server Environment for Effective Protection against Outages and Network Attacks
The cumulative outages of the Amazon Web Services and the attacks on the global DNS network have shown that even large and supposedly professionally protected networks are endangered, too. These incidents also make us aware of the need to distribute critical infrastructures across multiple cloud providers. This distribution is particularly important for centralized authentication services, […]
Use of Univention Corporate Server: Our 3rd Party Charts
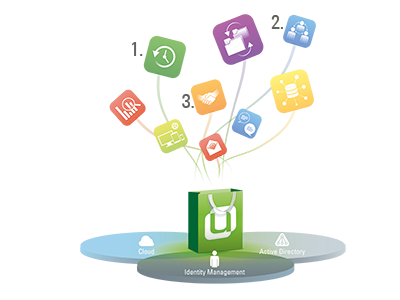
Thousands of organizations around the world use Univention Corporate Server every day. And the number increases week after week. The reason among others is that the Univention App Center contains, in addition to many UCS modules and extensions, dozens of professional enterprise applications from various vendors which can be easily integrated and maintained via the […]
ONLYOFFICE joins the Univention family
Users and providers of Univention Corporate Server now can add ONLYOFFICE Online Editors to their infrastructure from Univention App Center. ONLYOFFICE is now a part of the Univention App family and complements it with a full-scale collaborative suite that offers editors for text documents, spreadsheets and presentations. It is 100% compatible with Microsoft Office files […]
New: UCS 4.2 App Appliances in Own Corporate Branding
Our App Center team has been busy as usual, releasing four Apps from the Univention App Center as App Appliances. An App Appliance bundles UCS and an App in a virtual machine. The Appliances are available for the virtualization and cloud formats KVM, VMware, and VirtualBox. In addition to the pre-configured App, they also contain […]
Shed Light on the “IT jungle” with a Domain Controller

The professional structure of domains and the use of domain controllers bring order to IT infrastructures. This is especially important when organizations are growing rapidly. Professional domain management allows their IT to grow dynamically. Otherwise, the infrastructure becomes a kind of “patchwork carpet” of many small solutions and unorganized resources, some of which act independently […]
Univention Corporate Server 4.2-2 released

One of the highlights of the second point release of Univention Corporate Server (UCS) are the significant enhancements UCS 4.2-2 offers for managing services and apps that are hosted in public cloud services such as the Amazon Marketplace. Services installed on UCS can now be accessed directly without any further configuration effort. Our development department […]
Make an App: App Settings

Since the last update, there is a now a new feature in the Univention App Center: “App Settings”. It allows simple configuration of an App from within the Univention Management Console. We developed this new feature so as to allow App Providers to improve the integration depth of an App in UCS and simplify the […]
Brief Introduction: Identity and Access Management

In this brief introduction we want to give you an idea of some important concepts for identity and access management (IAM), and of the related challenges organizations face. We will also see how IAM is one of UCS strengths and why UCS is being adopted by large companies, and by governmental institutions, to manage tens […]