From Practice
New UCS training program

The Univention Corporate Server (UCS) technical training has long been an established and essential part of our service portfolio. It ensures the successful use of our products UCS and UCS@school in organizational IT. In a two-day seminar, our customers received a detailed introduction to UCS. They learned about its administration and configuration and were able […]
How does Single Sign-on work?
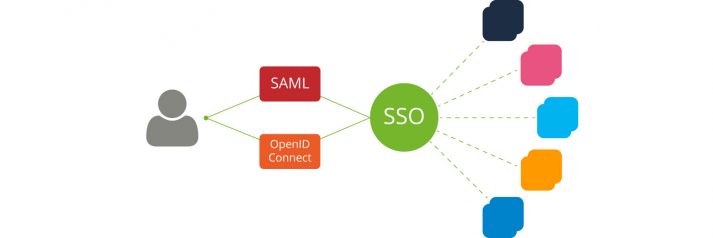
More about Identity and Service Providers, SAML, OpenID Connect and other technical Requirements for User Authentication Single sign-on (SSO) is an authentication process which allows users to log in to many different applications with only one set of credentials. They enter their username and password once and are automatically granted access to all programs and […]
Automatically manage Samba Shares in UCS and UCS@school

Whether you want to share files, printers or other services in your network – the Open Source software suite Samba is an incredible powerful tool which brings Linux, Windows and macOS client computers together. Samba can manage shares for users and groups, and since version 4, Samba can also take on the role of an […]
How to integrate with LDAP – Example Redmine

In the blog article series “How to integrate with LDAP”, we introduce a whole range of different options and possibilities for how you can use LDAP provided by UCS to expand or use in cooperation with other services. In the first section of this article, “Typical Configuration Options”, I will be using an example to […]
An introduction to DNS and its relationship with Univention Corporate Server
This article is about the Domain Name System (DNS) and explains how the “Internet’s telephone book” works. Alongside the fundamental details of name resolution on the Internet, we also look at special topics like administering DNS records in dynamic environments and debugging DNS setups during operation. We look at it within the technical framework of […]
Open Web Lounge 2020: learning how to fly with UCS, BigBlueButton and Cloudron
Can you imagine conducting an online event solely with self-hosted open-source tools and self-service? Or does that seem impossible to you? This article describes how we did just that by using UCS, Cloudron and BigBlueButton.
LDAP replication: ensuring fail-safe performance and reasonable load distribution

It is well-known among IT staff members: the administration tasks (for multiple applications and depending access rights) which apply even with a small amount of users can prove to be very time-consuming. With possible changes of responsibilities or the joining of new staff members, chances are high that uncontrolled growth arises quickly within the IT […]
Film Tutorial: How to Use User Templates in UCS
With user templates, Univention Corporate Server (UCS) offers a proven instrument to minimize the effort of IT admins. Who doesn’t know these slight doubts: Does the e-mail address of the new intern have the correct syntax? Has the new colleague been added to the right user group? The user templates help to dispel these and […]
LDAP: Last logon timestamp recordings with UCS

In relatively many UCS environments, system administrators have not yet developed consistent processes for detecting, deactivating or deleting inactive user accounts. Over the years, accounts that have not been used for a long time accumulate in the LDAP directory. At Univention, we have developed a new UCS extension on behalf of a customer, which helps […]
UCS Samba/AD: How to establish trust with native Microsoft Active Directory domains
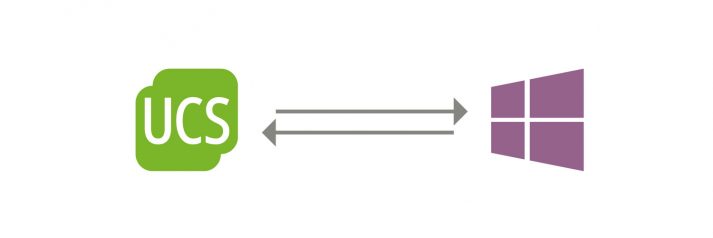
Establishing a trust relationship means giving users of a domain access to the resources of another domain. In some situations this can extend the options for identity management. In the following example, I will refer to the interaction between Samba in UCS and Microsoft Windows. I will explain in detail how a so-called trust relationship […]