Apps and Partners
UCS at the SchwuZ in Berlin, Part 2: Synchronizing User Profiles

We would like to inform you about further mile stones we achieved with our IT project at the Berlin-based cultural event organizer SchwuZ and therefore complement our last blog article bitpack.io modernizes IT at the SchwuZ in Berlin with Univention Corporate Server from last year with instructions on how to setup synchronized user profiles.
‘Vote for Apps’ End of 2. Round: Did Your Favorite Make It?

We’ve now finished the second round of the voting series ‘Vote for Apps’ in the Univention App Catalog which took place from February 9 to March 9. I thank all participants for their engagement and like to present the result today. This time, you were able to vote for the Apps Cozy Cloud, a service to […]
Minio – The secure alternative to Amazon S3 for object storage
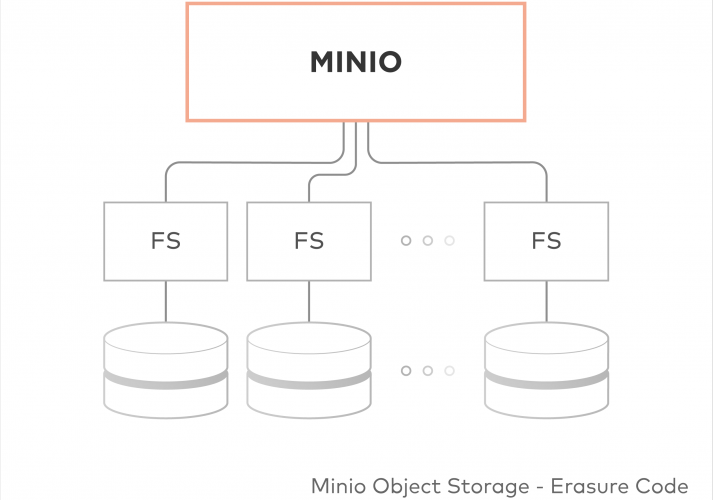
Shortly before the Univention Summit, I released the Minio app for the Univention App Center. The development of the app started after Univention introduced their Docker-based apps and Minio, as a single binary that does not need much external configuration, seemed like the perfect test case. As it turned out, it was.
3rd Party App Chart for February 2018

It’s time for a new edition of our 3rd Party App Charts. Compared to the last ranking in December the following changes occurred:
“Vote for Apps” End of 1. Round: Did Your Favorite Make It?
It’s been a while now we have introduced a new category to the App Catalog on our website called “Vote for Apps”. Here, we present Apps that are not yet available in the App Center but for which you can cast your vote. We thus want to find out which solutions are most useful for […]
Tine 2.0 Caroline Available – Full Text Search and Versioning

Welcome Caroline! If you ask yourself every year why Tine 2.0 Major releases are code-named Elena, Egon and now Caroline, just know that these are the names of the offspring of the Tine 2.0 team. And Caroline really has it in the bag. Our latest strike is our most comprehensive update to date. Here is […]
How to get happy with your groupware solution …

Groupware has become an indispensable part of our daily office routine. Connected data and teamwork is highly important for the success of a company. But every groupware user can think of a few things that could be optimized. Sure, what software is perfect? We at DIGITEC have identified a few missing features and have worked […]
Collaborative Cloud Workspace Based on Univention Corporate Server

In this success story, a team which had only worked together online in the past required a stable IT infrastructure of its own with classic, collaborative elements as well as a cloud workspace. Following successful realization of the project, the cooperation can now continue in a virtualized environment with UCS. In this article, I will […]
Central IdM of Cloud to Minimize Risks with Users and Structures

When administrators think about user management (IdM), they often only keep an eye on traditional IT systems. But even in the cloud, where you can buy new services with just a few clicks, it’s extremely important for companies to keep control over their users if they do not want to lose control over who has […]
I Mattermost now…

I wrote the following article about the ChatOps solution Mattermost on November 26, 2017 for my own Blog “gestreift.net”. As Mattermost has been available in the Univention App Center for a few months now, Univention had the idea to publish this article here for your information, too. And here we go: It’s just over a […]