From Practice
How to Integrate SAML Single Sign-On in ownCloud App
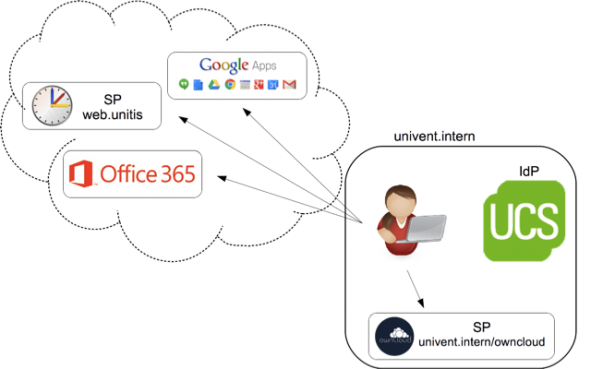
If you need to use various services online, which is by the way the norm, there’s nothing more conventient than using single sign-on (SSO). SSO allows you to log in to all available services in a domain with one password only. UCS provides this feature via the SAML Identity Provider since UCS 4.1. We chose to […]
Step by Step Guide to a Multi-Server Environment for Effective Protection against Outages and Network Attacks
The cumulative outages of the Amazon Web Services and the attacks on the global DNS network have shown that even large and supposedly professionally protected networks are endangered, too. These incidents also make us aware of the need to distribute critical infrastructures across multiple cloud providers. This distribution is particularly important for centralized authentication services, […]
Shed Light on the “IT jungle” with a Domain Controller

The professional structure of domains and the use of domain controllers bring order to IT infrastructures. This is especially important when organizations are growing rapidly. Professional domain management allows their IT to grow dynamically. Otherwise, the infrastructure becomes a kind of “patchwork carpet” of many small solutions and unorganized resources, some of which act independently […]
Make an App: App Settings

Since the last update, there is a now a new feature in the Univention App Center: “App Settings”. It allows simple configuration of an App from within the Univention Management Console. We developed this new feature so as to allow App Providers to improve the integration depth of an App in UCS and simplify the […]
RADIUS – a Powerful Tool for Safe Mobile Device Accesses

Workplaces become more remote and mobile while individuals are increasingly equipped with (private) mobile devices. In this context it is good to know about RADIUS, because private end devices require simple access to an organization’s network. At the same time you need to avoid that these devices open the doors for malware or leakage. RADIUS […]
OpenVPN to Secure your Samba Authentications Automatically

Samba 4 has become the tool of choice for companies with diverse clients that seek a Linux-based central identity management. However, a growing number of organizations are offering work from home options and manage distributed operations like construction companies with a computer at every construction site or an insurance provider with several offices. The securing of all authentication processes […]
UCS Identity Management Manages Mail Platform With Over 30 Million Users

More than two years after the start of one of the largest projects in which Univention has been involved to date, a new mail platform with over 30 million managed end users finally went online in late 2016. UCS takes care of the identity management duties for all the user accounts. I first reported on […]
Facilitate Your Work by Integrating Listener Modules in UCS

Listener modules support you in your administrative work by synchronizing and controlling all changes in the UCS’ OpenLDAP Einacross all connected services – Learn how to build and use them! You are surely using a variety of (cloud) services in your organization and, if required, these services will make changes to your directory service, either Active Directory […]
Secure Operation of Existing Applications in the Corporate Environment with Open Source Tools

Last year I submitted my Master’s thesis titled “Secure Operation of Existing Applications in the Corporate Environment with Open Source Tools”, and successfully earned my degree in IT from Bremen University of Applied Sciences. My research focused in particular on the differences and the security-related advantages/disadvantages of server virtualization compared with operating system virtualization, which […]
Ansible Modules for the Automation of UCS-Specific Tasks

As a long-term Univention partner, we at Adfinis Sygroup operate UCS environments for many of our customers. We employ Ansible for automation when running different Linux distributions as it standardizes the roll-out of UCS among other things. Up until now there weren’t any Ansible modules available for UCS-specific tasks. To remedy this, we developed modules […]