RADIUS (Remote Authentication Dial-In User Service) is a central component of UCS and enables you to control access to WLAN networks for users, groups, and devices. In January we published a blog post with a short introduction to RADIUS, and in this article I’m going to explain how to set up RADIUS for your UCS domain. This article also covers the new features in UCS 4.4.
What is RADIUS?
RADIUS handles the authentication of users and their authorization after logging in (i.e. access to certain data or services). It also takes care of creating log files. Advantages of this solution are that the users’ credentials (their domain passwords) are stored and managed at a central location (in the directory service). RADIUS enhances security for your networks and is therefore a good idea when you’re planning to set up a BYOD (Bring Your Own Device) environment, for example in companies or schools.
It’s easy to install RADIUS via the Univention App Center. In order to connect WLAN clients (such as laptops, smartphones, or tablets), the corresponding access point (AP) must support the IEEE 802.1x standard, i.e. WPA Enterprise. Store the RADIUS server’s information in the AP configuration, and users can now connect with the same usernames/passwords they use in the UCS domain.

How-To: Securing Networks with RADIUS
Bringing Your Own Device (BYOD) is popular, but before users connect to the school or corporate Wi-Fi with their personal devices, administrators should think about security so that the devices do not become a gateway for malware… read more
New Features for RADIUS in UCS 4.4
UCS 4.3 (and previous versions) included the package. After installing it, for example via the App Center, you had to adjust the configuration on the command-line. The new version in UCS 4.4 makes things a lot easier. We’ve added a standard configuration for the RADIUS server and it’s possible to customize it via the graphical Univention Management Console (UMC).
In UCS@school 4.3 (and previous versions) you had to install an additional RADIUS package (ucs-school-radius-802.1x) that provided you with the necessary configuration snippets for schools. We’ve included this functionality in the univention-radius package, and the UCS@school package for 4.4 has been revised. It now includes an add-on for the RADIUS app (proxy setup) and depends on the univention-radius package.
For more information, please have a look at the release notes for UCS 4.4 and UCS@school 4.4.
Migrating UCS 4.3 to UCS 4.4
During the upgrade from UCS 4.3 to version 4.4, existing configuration files are not being migrated automatically. An existing clients.conf file (AP configuration) is not overwritten or deleted. Configuring RADIUS via the Univention Management Console of UCS 4.4 results in a clients.univention.conf file. It’s a good idea to either use UMC or the command-line – don’t mix up both methods.
Configuring RADIUS via the UMC
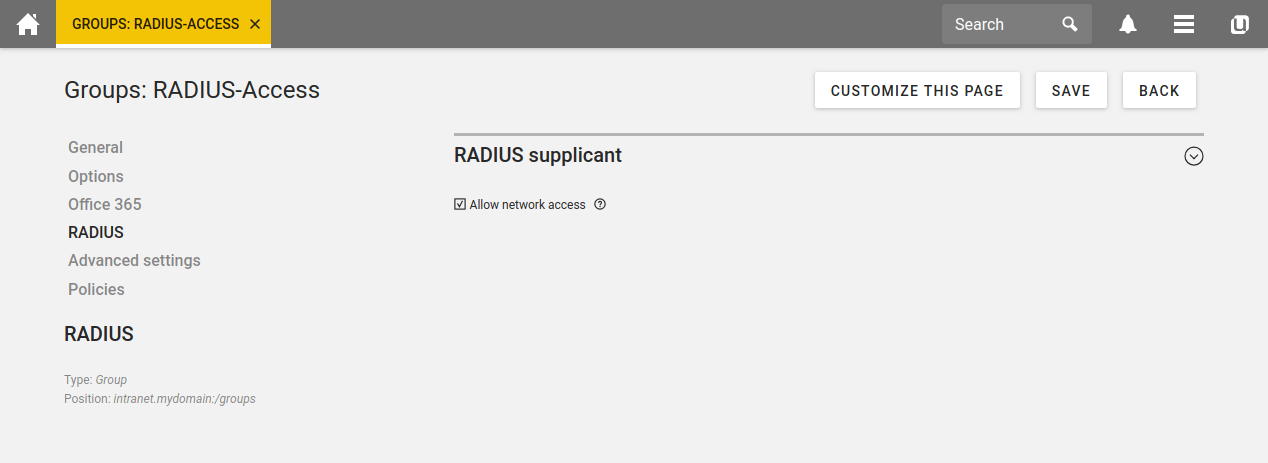
After installing RADIUS in the Univention App Center, the FreeRADIUS software is good to go. Next, you need to configure WLAN access for users or groups. Open the configuration of a user object, click on the RADIUS tab on the left, and enable the checkbox “Allow network access”. This checkbox also exists in the configuration dialog for groups, so that all members automatically have access to the WLAN.
All Access Points must be known to the RADIUS server. In the Univention Management Console create a new computer object for each AP, select Options from the menu, and activate the checkbox RADIUS Authenticator. Click RADIUS on the left side and enter the IP address and the Shared secret.
All APs configured through the UMC are known to the RADIUS servers of the domain. After you’ve clicked Save, the Univention Directory Listener writes the file /etc/freeradius/3.0/clients.univention.conf and the RADIUS server is being restarted (after about 15 seconds). Newly added access points have access to the RADIUS server after the restart.
Troubleshooting the RADIUS Server
UCS 4.4 includes improved troubleshooting features. The command-line tool univention-radius-check-access checks current access rules for users and MAC addresses. Simply enter the command as user root in a terminal on your UCS server.
The log file of the RADIUS server is /var/log/univention/radius_ntlm_auth.log. The Univention Configuration Registry variable freeradius/auth/helper/ntlm/debug determines how detailed the messages in the log file are. The log file of the FreeRADIUS server is stored in /var/log/freeradius/radius.log. Fore more information, please refer to the UCS manual.


Comments
Eric Browning
Thanks for the enhancement with freeradius. How about making dynamic VLAN assignment a part of it too. Devices like wifi payment systems have PCI requirements that staff laptops don’t and as such need to be placed on another VLAN (dynamically, *hint hint*).
Andreas Peichert
Hello Eric, the trick is if you want to have multiple VLAN with radius, you have to set up one WLAN SSID per VLAN, see
https://help.univention.com/t/q-a-can-i-use-radius-to-assign-clients-to-different-vlans/14342
each VLAN can have its own properties i.e. DHCP, DNS etc.
https://help.univention.com/t/howto-configure-dhcp-server-with-policies-and-multiple-vlans/13535
Feel free to ask at our forum, if you have any issues with this
https://help.univention.com/
lephisto
Hello Andreas,
what you are writing is not true. Having one SSID per VLAN doesn’t scale, because an increased number of ssids reduces throughput because of enormous Amount of beacon Frames required.
In my current environment which I’m planning to move to UCS in the near future, we have one SSID and the VLAN assigned to the Client is determined with the Radius Attribute “radiusTunnelPrivateGroupId” and “radiusTunnelType” set to VLAN, which is accordingly mapped to the matching ldap Attribut.
It would be nice to see support for this in UCS.
Andreas Peichert
Hello lephisto, having one WLAN SSID per VLAN does work. To reduce the complexity we leave VLANs to the network layer. But I’ll go with you if that’s not ideal for your purpose.
The Attributes “radiusTunnelType” and “radiusTunnelPrivateGroupId” are part of objectclass “radiusprofile”, which is not included by default. But I think that could be done by two simple steps. But i havn’t tested it by my self:
1) To “use” the schema: Load it into ldap (/usr/share/doc/freeradius/schemas/ldap/openldap/freeradius.schema.gz)
2) To “edit” the values: Add both keys as Extended Attributes to the User/Computer (https://docs.software-univention.de/manual-4.4.html#central:extendedattrs)
Feel free to start a question in our forum, if you need some help: https://help.univention.com/
Urs Aregger
Hi lephisto
I‘m planning a similar setup. Also on the wired part of the network.
I‘d like to read and learn how to do it with Univention.
Thanks for your how-to