Let’s talk about VLANs—in this article I would like to talk about virtual networks and their benefits. I’m also going to describe how configure VLANs in Univention Corporate Server (UCS), how to increase security for your UCS environment with our RADIUS app and dynamically assign devices to specific VLANs via a RADIUS server.
Table of Contents
What are VLANs anyway?
Virtual Local Area Networks (VLANs) divide existing physical networks into several logical networks. They are used to separate data traffic at network level. Each VLAN has its own unique VLAN ID and creates its own broadcast domain, i.e. its own logical group of network devices in the LAN (local area network). Devices in different VLANs can therefore only communicate with each other via a router that is also connected to both virtual networks.
VLANs are often used in large environments, such as in companies or on campus at schools, colleges, and universities. For example, admins in corporate networks provide separate networks for employees and guests—without having to change the cabling or set up additional WLAN routers. Some companies divide their networks into VLANs for the different departments, such as marketing, sales, etc.
Splitting up networks can be helpful for a number of reasons. Isolated subnets not only increase security, but also affect the performance. For better bandwidth management, VLANs can separate externally accessible services such as web servers from other services on the same network. Services for communication such as VoIP (Voice over IP) can also be accessible via dedicated VLANs, which then have a higher priority in the same physical network.
How to configure a VLAN on Univention Corporate Server (UCS)
You configure virtual networks for your UCS domain via the Univention Management Console (UMC), in the System / Network settings module. After clicking on Add, select Virtual LAN as the Interface type and specify the Parent interface.
Enter a VLAN ID, a unique identifier for the virtual network. Valid values range from 1 to 4095. Click the Next button. Now assign an IP address to the VLAN interface. Make sure that it matches the assigned VLAN address range.
UCS Manual
For more information on configuring IPv4 and IPv6 addresses, please refer to the UCS manuel.
To assign users and groups to specific VLANs, you can additionally set up a RADIUS server. This server then handles the authentication of the users and returns a VLAN ID in response. In the next two sections, I’ll briefly explain how to achieve this under UCS.
RADIUS: Authentication Methods for Wired and Wireless Networks
With RADIUS (Remote Authentication Dial-In User Service), you can configure access control for networks—not only for WLAN networks, but also for wired networks. RADIUS is implemented as a client-server architecture. The RADIUS server first checks whether someone is authorized to access the network. It handles authentication and authorization for users and groups. The RADIUS server’s clients are WLAN access points, network switches, etc. The users’ end devices (laptops, tablets, smartphones, etc.) do not talk directly to the RADIUS server.
With RADIUS, you can ensure that only authorized users can access a network. For more information, see our blog article How-To: Securing Networks with RADIUS.
Setting up RADIUS on UCS
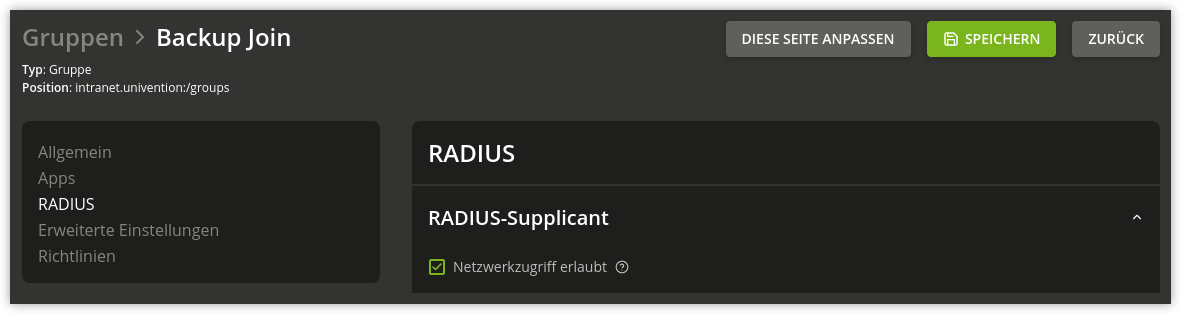
In our Univention App Center, we provide the open source RADIUS server FreeRADIUS as an app for UCS. The service is configured to connect to the UCS LDAP directory service. After installation, you can allow users and groups access via the RADIUS menu item and clicking the checkbox Allow network access.
The FreeRADIUS app also provides deny and allow lists for user accounts, groups, and devices—all with just a few clicks in the UCS management console.
By default, users authenticate with their domain password. Alternatively, it is possible to create an extra password for RADIUS by setting the UCR variable radius/use-service-specific-password. In order for users to (re)set this password via our self-service, the UCR variable umc/self-service/service-specific-passwords/backend/enabled must be set to true>/code>.
Tip: You can set up MAC address filters and only allow certain devices to connect. To learn more about this topic, please read the corresponding chapter in our manual.
RADIUS and VLAN IDs
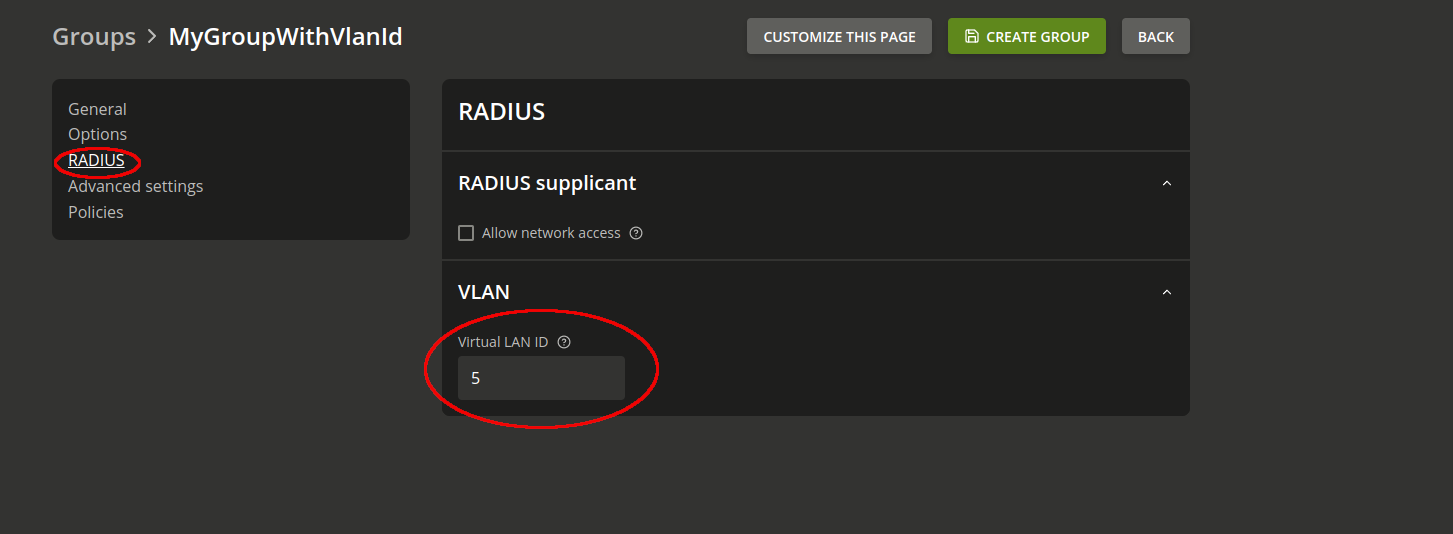
It’s possible to configure UCS so that the system returns a VLAN ID in the RADIUS authentication process. All you need to do is assign a group to a specific VLAN ID.
You can also configure a default VLAN ID which is returned as a replacement ID if a user account is not a member of a group with a VLAN ID. You set the default VLAN ID using the UCR variable freeradius/vlan-id.
Conclusion
You can conveniently configure VLANs, RADIUS, VLAN IDs, and more in the Univention Management Console, increasing security through advanced access controls.
Do you have any questions or other feedback? Feel free to leave a comment below this article.

Comments
Eric Browning
What would be nice is if UCS supported a newer version of Freeradius that support TLS 1.3 so I don’t have to deal with the nonsense of Windows 22H2’s mandatory use of TLS 1.3.