The Gateway to your IT – (New) Functions of the UCS Portal
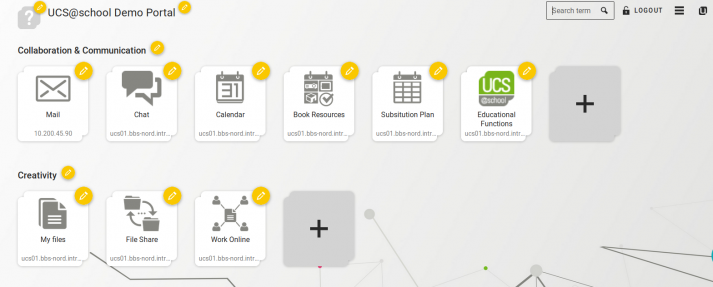
For some time now, the portal with its modern appearance and easy administration has been the central entrance to a UCS domain for users and administrators alike. My colleague Johannes has already described the most important functions of the portal in our article How to Configure the UCS Portal Easily with Drag & Drop. With UCS 4.4, we added some new features which I would like to introduce you to in this article.