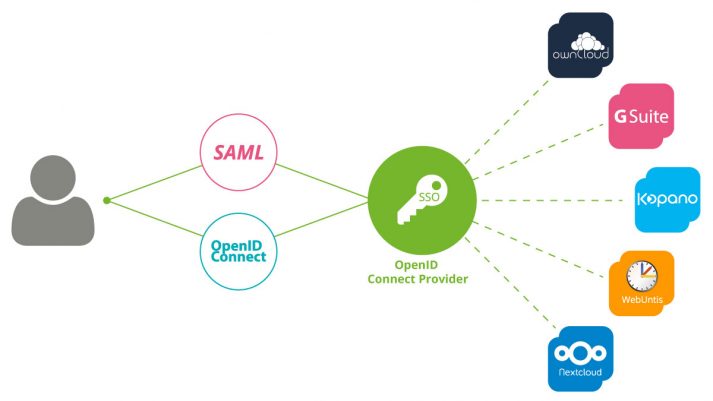
The integration of Kopano Konnect in the single sign-on network of Univention Corporate Server is an additional option for users to access a range of various applications that are integrated in UCS via a single, initial login using their user name and password.
The two authentication standards SAML (Security Assertion Markup Language) and OpenID Connect have already been available to UCS users for some time. So far, however, these two technologies have been two separated worlds. If some of the web services used SAML and others OpenID Connect for the authentication against UCS’ identity management, users were forced to log in twice in those environments with multiple services. With the support of the Kopano team, we were able to release an extension of the app “OpenID Connect ID” in the App Center. This is integrating the two standards with each other and thus allows a single authentication process by the end user.
I would like to briefly explain how a single sign-on generally works with UCS. Then I explain the interaction of Kerberos, SAML, and OpenID Connect and show you which functions the new implementation of Kopano Konnect offers to UCS users.
What Does “Single Sign-on” Mean?
With a single sign-on, the user logs on to the desktop computer in the domain and can then directly access other services such as file and print servers. The user only need to authenticate him- or herself once to an entity (server) (e.g. by entering a password or other factors) and then the SSO mechanism takes over the authentication against further services transparently in the background.
After the authentication, the user usually receives a data packet called ticket, token or cookie, which serves for a limited period (“session”) as an access key for authentication to the other services. The SSO mechanism stores the access key and ensures that the key is provided at the right time. Hence, the users only need to enter their user name and password once.
SAML and OpenID – Decentralized and Web-based Single Sign-on
OpenID and SAML are decentralized and web-based single sign-on systems, in which the users must have authenticated themselves with an identity provider (IDP) in order to subsequently access the connected services – so-called service providers (SP) – such as websites.
At the authentication service, the user’s browser receives a temporary session cookie with which he or she can access the integrated internal and external services. This process is secured by the signature of the session cookie, which is based on keys or certificates previously exchanged between IDP and SP.
Kerberos – Network-based Single Sign-on Protocol
Kerberos, in turn, is a single sign-on protocol that is designed in such a way that participating systems are connected in the same network. A client authenticates with the Kerberos server and receives a ticket (TGT – Ticket Granting Ticket). This ticket can then be used to call up additional tickets for various services.