Integrate Nextcloud manually into UCS
However, the Docker-based integration has a few disadvantages due to its architecture, for which a Nextcloud installation on a different platform would be worth considering.
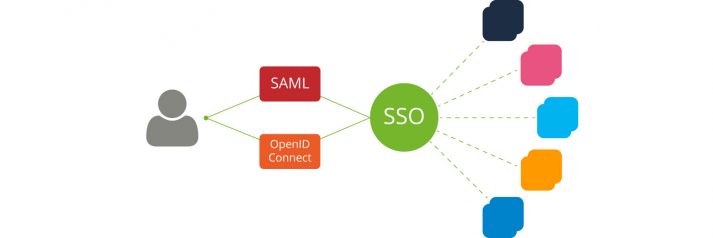
How does Single Sign-on work?
Single sign-on (SSO) is an authentication process which allows users to log in to many different applications with only one set of credentials. They enter their username and password once and are automatically granted access to all programs and services which have been made available to them. After they have authenticated successfully for the first time, the SSO mechanism takes over and handles the authentication to all the other services.
Automatically manage Samba Shares in UCS and UCS@school
Healthcare IT Infrastructure: Requirements and key elements
In the healthcare sector, highly sensitive data is handled every day and must be protected against unauthorized access. A modern IT infrastructure with relevant key elements increases trust and security for patients. Kevin Dominik Korte, President of Univention North America, reports on the requirements of such an IT infrastructure on the renowned US magazine Forbes.
In his article, Kevin Korte highlights five key elements that can help to make an IT infrastructure scalable, secure, and user-friendly.
The full article is available on forbes.com.